APIs are the spine of recent software program methods. They permit completely different functions and providers to speak with one another, enabling the whole lot from cell apps to cloud platforms to operate easily. Nevertheless, with this energy comes danger. APIs, if not correctly secured, can turn out to be straightforward targets for attackers, resulting in severe safety breaches, information leaks, and repair disruptions.
For builders and corporations in search of API growth providers, understanding API safety is essential to defending functions from these threats. Securing APIs not solely safeguards your app but in addition ensures the protection of your customers’ information.
The purpose of this weblog is to elucidate the significance of API safety and supply steering on methods to shield your functions from widespread API-related threats. We’ll focus on vulnerabilities, greatest practices, and instruments that may assist you safeguard your APIs in opposition to assaults. By the tip, you’ll be geared up with the information wanted to successfully safe your APIs and improve the general safety of your functions.
Understanding API Safety
What’s an API?
An API (Software Programming Interface) is sort of a messenger that helps completely different software program functions talk with one another. Consider it as a bridge that permits one program to ship or request info from one other. For instance, whenever you use a cell app to verify the climate or e-book a experience, the app is utilizing an API to get the knowledge from one other system or service.
Why APIs are a Goal for Attackers
APIs are engaging to attackers as a result of they act as a direct gateway to useful information and providers. Listed here are two essential explanation why APIs are focused:
- APIs expose delicate information: APIs present entry to essential information, similar to person particulars, monetary transactions, or enterprise operations. If an attacker can break into an API, they’ll steal or misuse this information.
- Widespread use: As extra firms depend on APIs throughout varied industries (from banking to healthcare), the variety of APIs in use has exploded. This enhance means there are extra alternatives for attackers to search out weaknesses and exploit them.
Key Safety Considerations for APIs
When fascinated by API safety, you want to pay attention to a number of dangers:
- Unauthorized Entry: If safety measures are weak, hackers can entry the API with out permission and steal information or manipulate the system.
- Information Breaches: Poorly protected APIs can expose delicate information like private info, monetary particulars, or proprietary enterprise information.
- DDoS (Distributed Denial of Service) Assaults: Attackers can overwhelm an API with a flood of requests, inflicting the service to decelerate or cease functioning.
- API Abuse and Misuse: Generally, even professional customers may misuse APIs by making too many requests or utilizing them in ways in which weren’t meant, which might disrupt providers or trigger efficiency points.
By understanding these dangers, you may construct safer APIs and higher shield your functions.
Finest Practices to Safe Your APIs
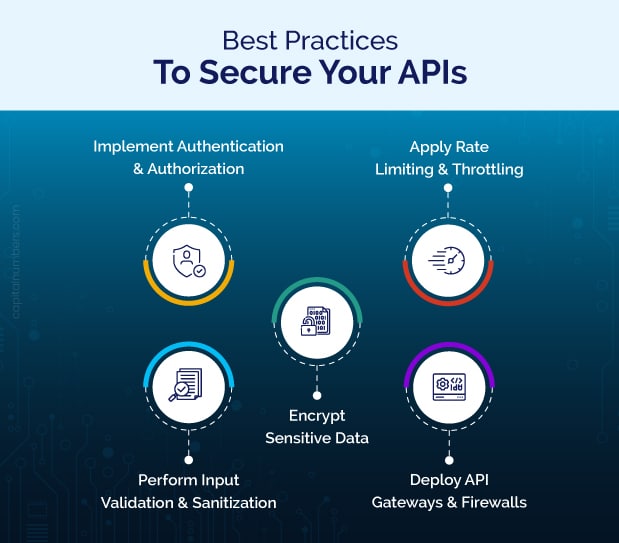
1. Use Robust Authentication and Authorization
You’ll want to ensure that solely the precise folks can entry your API. Right here’s how you are able to do that:
- OAuth 2.0 and OpenID Join: These are safe strategies for verifying the id of customers. OAuth 2.0 permits customers to log in securely utilizing accounts from platforms like Google or Fb with out sharing their passwords. OpenID Join is constructed on prime of OAuth 2.0 and provides extra safety by verifying person identities.
- Position-Primarily based Entry Management (RBAC): RBAC ensures that customers can solely entry the elements of your API which can be related to their roles. For instance, an admin might need entry to extra API capabilities than an everyday person.
- Scope Validation: This includes checking what actions or sources a person is allowed to entry based mostly on their permissions (scope) and making certain they don’t exceed these limits.
2. Encrypt Information
At all times shield the information touring between purchasers (like net browsers or cell apps) and your API:
- TLS (HTTPS): It is best to all the time use HTTPS (which makes use of TLS encryption) to verify the communication between purchasers and your API is safe. This prevents attackers from intercepting delicate info.
- Encryption for Delicate Information: Not solely do you have to encrypt information whereas it’s being despatched (in transit), however you also needs to encrypt it when it’s saved (at relaxation) to guard it from being accessed by unauthorized customers.
3. Fee Limiting and Throttling
You’ll want to stop customers or attackers from overloading your API with too many requests, which might crash your system or make it sluggish.
- Fee Limiting: This limits what number of instances a person or system can name your API inside a sure timeframe. This may shield you from abuse, similar to DDoS (Distributed Denial of Service) assaults the place attackers flood your API with requests.
- Throttling: If a person exceeds the speed restrict, you may decelerate (throttle) their entry to the API quite than fully block them. This helps guarantee truthful utilization.
4. Enter Validation and Sanitization
Make sure that all enter coming into your API is protected and clear:
- Enter Validation: Earlier than processing any information from customers, confirm that the information is within the appropriate format and doesn’t include something surprising. For instance, if a area expects a quantity, be sure that the enter is definitely a quantity.
- Sanitization: This includes cleansing the enter to take away probably dangerous characters or code (like scripts or SQL instructions). This helps stop assaults similar to SQL injection or cross-site scripting (XSS).
5. API Gateway and Firewalls
These instruments act as guards to your API, including an additional layer of safety:
- API Gateway: An API gateway sits between customers and your API, managing issues like authentication, authorization, and monitoring. It acts as a single level of entry, making it simpler to implement safety insurance policies throughout all API requests.
- Internet Software Firewall (WAF): A WAF helps detect and block malicious visitors earlier than it reaches your API. It could possibly shield your API from widespread assaults similar to SQL injection or DDoS assaults by analyzing incoming visitors and filtering out something dangerous.
By following these greatest practices, you can also make your APIs far more safe and cut back the chance of assaults or information breaches.
Safe API Design Ideas
1. Precept of Least Privilege (PoLP)
This precept implies that your API ought to solely be allowed to entry the information and sources it completely wants, and nothing extra. By limiting entry, even when somebody hacks your API, the quantity of injury they’ll do can be restricted.
- Instance: In case your API is supposed to indicate person profiles, it ought to solely be capable to entry profile info and never have entry to issues like fee particulars or admin settings. By limiting entry, you cut back the chance if one thing goes improper.
2. Safe API Endpoints
API endpoints are the precise URLs or addresses the place your API will be accessed (like https://yourapi.com/person/profile). Securing these endpoints is essential to guard your API from assaults.
- SSL/TLS Encryption: At all times use SSL/TLS (i.e., HTTPS) to encrypt the communication between your API and its customers. This prevents attackers from intercepting delicate information.
- Larger Authentication for Delicate Operations: For actions that contain delicate info or essential capabilities, like deleting information or processing funds, require stronger authentication (similar to multi-factor authentication or particular permissions).
3. Versioning Your APIs
Once you replace your API with new options or safety enhancements, it’s essential to handle completely different variations correctly. Versioning lets you make modifications with out breaking the prevailing functions which can be utilizing the older variations of your API.
- Instance: For those who launch model 2 of your API however some customers are nonetheless utilizing model 1, you may preserve each variations (like https://yourapi.com/v1/useful resource and https://yourapi.com/v2/useful resource) to make sure that the whole lot continues to work easily. This additionally helps you apply safety patches to particular variations with out affecting others.
By following these ideas, you may design your APIs to be safer and higher shielded from potential threats whereas making certain they continue to be versatile and simple to handle.
Instruments and Applied sciences for API Safety
1. API Safety Testing Instruments
To ensure your API is safe, you want instruments to check for vulnerabilities and potential weaknesses. Listed here are some helpful instruments you should use:
- OWASP ZAP: This can be a free device that helps you discover safety points in your API. It could possibly routinely scan your API for widespread vulnerabilities, like injection assaults or safety misconfigurations.
- Postman with Safety Assessments: Postman is a well-liked device for testing APIs. Along with common API testing, you may arrange safety assessments to verify for issues like authentication errors or surprising information entry.
- Burp Suite: This can be a highly effective device used to scan for API vulnerabilities. It helps you establish safety flaws, similar to damaged authentication or information leaks, by simulating assaults in your API.
2. API Administration Platforms
These platforms assist you handle, monitor, and safe your API from a central place. They deal with issues like authentication, charge limiting, and logging:
- Apigee: A device that helps you handle APIs by imposing safety insurance policies, managing entry management, and monitoring utilization. It lets you safe your API whereas additionally making it straightforward to scale.
- Kong: Kong is one other fashionable platform that secures your API by managing entry management, establishing charge limiting, and logging API exercise. It’s designed to deal with large-scale APIs.
- AWS API Gateway: This device from Amazon Internet Companies helps you handle APIs by controlling who can entry them and making use of security measures like authentication and monitoring. It’s particularly helpful in case your API is hosted within the AWS cloud.
3. Risk Detection and Monitoring
As soon as your API is dwell, it’s essential to constantly monitor its exercise to detect any suspicious conduct or potential threats. These instruments may also help:
- DataDog: A monitoring device that helps you monitor API efficiency and detect any uncommon or malicious exercise, similar to unauthorized entry makes an attempt or efficiency slowdowns.
- Splunk: A device that collects and analyzes information out of your API, permitting you to identify any safety points or anomalies. It helps you monitor for threats in real-time.
- CloudTrail: For those who’re utilizing AWS, CloudTrail helps monitor each API name made in your surroundings. It information who accessed your API, what they did, and once they did it, which helps you detect and reply to threats rapidly.
Through the use of these instruments and platforms, you may higher safe your APIs, monitor their efficiency, and rapidly establish any safety threats.
API Safety within the Cloud
Cloud-Particular API Safety Challenges
When your APIs are hosted within the cloud, there are a number of further safety challenges you’ll want to take into consideration:
- Shared Accountability Mannequin: Within the cloud, safety is a shared accountability between you and your cloud supplier. This implies the cloud supplier (like AWS or Google Cloud) handles the safety of the infrastructure (like servers and networks), while you’re accountable for securing your APIs, information, and functions. Understanding the place your accountability begins is vital to making sure correct safety.
- Hybrid Environments (Cloud and On-Prem): Many firms use each cloud-based providers and on-premises (in-house) methods. Managing safety throughout these environments will be tough as a result of you must safe each your cloud-based APIs and your on-prem methods, making certain they impart securely with none weak factors.
Safety Finest Practices in Cloud-Primarily based APIs
To maintain your APIs safe within the cloud, listed below are some greatest practices you may observe:
- Use Identification and Entry Administration (IAM): IAM is a device that helps management who can entry your APIs and what they’re allowed to do. With IAM, you may set guidelines for various customers or providers, ensuring solely approved folks or methods can work together together with your API. For instance, you may make sure that solely particular staff or apps can entry delicate API capabilities.
- Make use of Cloud-Native Safety Instruments: Cloud suppliers supply instruments designed particularly to guard your APIs. For instance:
- AWS Protect: This device helps shield your APIs from DDoS (Distributed Denial of Service) assaults, the place attackers flood your API with visitors to overwhelm it.
- Google Cloud Armor: This device protects your APIs from varied varieties of assaults by blocking suspicious visitors and preserving your API safe from threats like SQL injection or cross-site scripting (XSS).
By understanding these cloud-specific challenges and utilizing the precise instruments, you may higher safe your APIs and shield your functions within the cloud surroundings.
You Could Additionally Learn: 12 Finest Practices to Safe Your API within the AWS Cloud
The Way forward for API Safety
AI and Machine Studying for API Safety
Synthetic Intelligence (AI) and Machine Studying (ML) are altering the best way we strategy API safety. These applied sciences assist make safety smarter and extra environment friendly:
- Predictive Analytics: AI can analyze massive quantities of information out of your API and search for patterns that may point out a safety danger. For instance, it might probably detect uncommon conduct, like a person immediately making too many API requests, and predict when an assault may occur earlier than it causes injury.
- Automated Risk Detection: Machine Studying can routinely establish new and rising threats by constantly studying from previous assaults and safety breaches. This implies your API safety can enhance over time, changing into more practical at stopping assaults without having fixed guide updates.
Zero Belief Safety Fashions
Up to now, as soon as customers or methods have been trusted, they have been allowed to entry many elements of an API. With the Zero Belief mannequin, the concept is that you must by no means belief anybody or something by default, even when they’re inside your system.
- “By no means Belief, At all times Confirm”: Which means that each person, system, or machine making an attempt to entry your API have to be constantly verified, regardless of the place they’re. For instance, even when a person is inside your community, they nonetheless want to offer proof (like multi-factor authentication) each time they attempt to use delicate API capabilities.
- Steady Monitoring: APIs following the Zero Belief mannequin are continuously monitored for any suspicious exercise, making certain that nobody can entry greater than they need to, and that any potential menace is detected immediately.
Shift-Left Safety
Shift-Left Safety means fascinated by and addressing safety earlier within the growth course of, quite than ready till the tip.
- Incorporating Safety Early: As a substitute of testing your API for safety points solely after it’s constructed, you must begin incorporating safety practices at first of the event cycle. This contains including safety assessments to your code because it’s written, reviewing API design for safety flaws early, and ensuring everybody on the event crew understands safety greatest practices.
By shifting safety “left” (earlier within the course of), you may catch and repair safety points earlier than they turn out to be larger issues in a while. This protects effort and time whereas making your APIs far more safe from the beginning.
You Could Additionally Learn: How you can Select the Proper API Improvement Firm
Conclusion
APIs are important for contemporary functions however can pose safety dangers like unauthorized entry, information breaches, and DDoS assaults if not correctly protected. Optimizing API safety is essential to safeguarding your functions and person information. Finest practices embody utilizing OAuth 2.0 for authentication, HTTPS for encryption, charge limiting to forestall overloads, and securing endpoints. Instruments like API gateways, net software firewalls (WAFs), and cloud-based safety may also help improve safety. API safety is an ongoing effort, serving to you keep resilient in opposition to evolving threats.
Involved about API vulnerabilities? Our API growth and integration providers guarantee your functions are safeguarded in opposition to threats. Contact us at this time to learn the way we may also help improve your API safety.

