In at present’s digital world, cyberattacks are a continuing risk. For builders, constructing safe software program isn’t non-obligatory – it’s elementary. A single software program vulnerability can have devastating penalties, resulting in exposing person knowledge, disrupting operations, and damaging your status. What do you do to make sure safe software program growth?
We’ll present a complete guidelines for software program safety finest practices, overlaying every part from guaranteeing safe coding practices to securing APIs. By following these practices, you’ll be able to scale back the chance of breaches and guarantee your functions stand robust. So, take management of your software program’s safety and construct with confidence – don’t get hacked!
Why Is Software program Safety Guidelines Important?
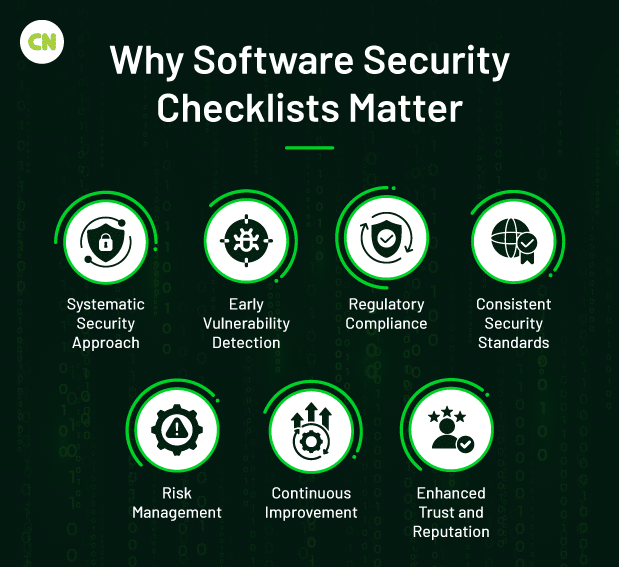
Implementing a software program safety guidelines is essential for organizations to guard their digital property and make sure the integrity of their software program options. Listed below are the important thing the reason why a software program safety guidelines is significant:
- Systematic Safety Method: A guidelines offers a structured framework for addressing safety all through the software program growth lifecycle (SDLC). It ensures no essential safety measures are neglected.
- Early Vulnerability Detection: It permits the early identification of potential safety vulnerabilities and dangers. This permits for well timed mitigation earlier than software program deployment, lowering the probability of exploitation.
- Regulatory Compliance: Many industries are ruled by strict knowledge safety and privateness rules. A complete safety guidelines helps guarantee adherence to those rules, avoiding potential fines and authorized points.
- Constant Safety Requirements: A software program safety guidelines ensures that safety measures are uniformly utilized throughout all organizational tasks and groups. This fosters a constant and excessive customary of safety practices.
- Threat Administration: By systematically addressing safety considerations, a guidelines helps handle efficient threat. It prioritizes areas of excessive threat and effectively allocates assets to deal with them.
- Steady Enchancment: Safety checklists could be recurrently up to date and refined in response to rising threats and new safety insights. It contributes to a tradition of fixed enchancment in safety practices.
- Enhanced Belief and Fame: Demonstrating a dedication to safety via adopting a complete safety guidelines can improve belief amongst clients and stakeholders. This positively impacts a company’s status.
Software program Safety Guidelines for Builders
1 Code Add Procedures
The code add procedures embody essential steps to safeguard and streamline growth processes.
For SFTP/FTPS Uploads
- The setup on a Linux server includes configuring SFTP or FTPS protocols, that are important for safe file transfers. This methodology prevents unauthorized entry and knowledge breaches by encrypting the information throughout transmission.
- Creating digital person areas for every undertaking is one other very important step, offering builders with a devoted and safe workspace. This method enhances safety by isolating undertaking environments and bettering group, making managing a number of tasks simpler.
- Integrating with an online server setup, comparable to Apache, Nginx, or Tomcat, offers builders a streamlined setting to deploy and check their internet functions instantly. This seamless integration is essential for environment friendly growth workflows because it facilitates instant suggestions and permits sooner iteration cycles. By leveraging established internet server applied sciences, builders can simply deploy and check their functions, resulting in faster growth cycles and improved productiveness. This integration additionally ensures compatibility with industry-standard server configurations, enhancing the scalability and reliability of internet functions.
For GIT Uploads
- Guaranteeing project-specific personal entry to GIT repositories is key to defending the codebase. Limiting entry to approved staff members prevents unauthorized viewing or alteration of the code, thereby safeguarding mental property and sustaining the undertaking’s integrity.
- This managed entry additionally facilitates a safe collaboration setting, the place builders can work collectively on code adjustments whereas guaranteeing that each contribution is tracked and managed correctly. That is essential for sustaining code high quality and facilitating efficient staff collaboration.
2 Code Scanning Practices
Code scanning practices are very important for guaranteeing the safety and high quality of software program growth tasks. These practices embrace a number of key parts:
Stopping Delicate Information Publicity
- Utilizing instruments comparable to ‘.gitignore’, ‘git secrets and techniques’, and ‘trufflehog’ is essential for safeguarding delicate info like credentials and confidential knowledge. ‘.gitignore’ helps exclude information from being dedicated to Git repositories, lowering the chance of by accident pushing delicate knowledge. ‘git secrets and techniques’ scans for secrets and techniques being uploaded, and ‘trufflehog’ searches via git histories for top entropy strings and secrets and techniques, stopping potential knowledge breaches.
- This observe is important for sustaining the safety integrity of codebases, guaranteeing that delicate knowledge isn’t uncovered to unauthorized customers or the general public, thereby mitigating dangers related to knowledge leaks and safety vulnerabilities.
Docker Picture Safety
- Using container scanning instruments like ‘Trivy’ and ‘Snyk’ is crucial for figuring out vulnerabilities inside Docker photos. These instruments scan for identified vulnerabilities throughout the container photos and dependencies, providing insights and proposals for remediation.
- Docker picture safety is a essential side of containerized software growth, guaranteeing that the deployment setting is free from safety flaws that attackers might exploit, thereby safeguarding the appliance infrastructure.
Code High quality Checks
- Utilizing ‘Sonarqube’ for steady inspection of code high quality is a proactive method to sustaining excessive requirements in software program growth. Sonarqube evaluates code for potential bugs, code smells, and safety vulnerabilities, apart from assessing code protection parameters to make sure thorough testing.
- Implementing code high quality checks is essential for the event lifecycle, enhancing the reliability and maintainability of the code. It helps builders establish and resolve points early in growth, resulting in safer, environment friendly, and high-quality software program merchandise.
3 Backend Infrastructure Safety
Backend Infrastructure Safety is a cornerstone in safeguarding internet functions and companies from cyber threats. Efficient measures embrace
Imposing HTTPS
- Transitioning from HTTP to HTTPS is key for enhanced safety. HTTPS encrypts knowledge in transit, stopping interceptors from understanding the visitors between a shopper and server. This encryption is facilitated by SSL/TLS protocols, which not solely shield the information integrity and privateness but additionally authenticate the visited web site.
- Imposing HTTPS is essential for all internet companies, because it ensures that delicate info like login credentials, private knowledge, and transaction particulars are securely transmitted, thus safeguarding in opposition to eavesdropping and man-in-the-middle assaults.
Firewall Safety
- Implementing Internet Software Firewalls (WAF) offers a protecting barrier for internet functions by filtering, monitoring, and blocking malicious HTTP/S visitors to and from an online service. WAFs are configured to guard in opposition to varied internet software vulnerabilities comparable to SQL injection, cross-site scripting (XSS), and different OWASP Prime 10 threats.
- Firewall safety is significant for sustaining web site safety, defending in opposition to focused assaults that would compromise the appliance and knowledge, thereby guaranteeing the integrity and availability of internet companies.
Safe Content material Supply
- Using Content material Supply Networks (CDN) for caching enhances internet service efficiency and safety. CDNs distribute the service spatially relative to end-users, bettering web site load instances and lowering bandwidth prices. Furthermore, using pre-signed URLs for static content material on companies like Amazon S3 provides an additional layer of safety, guaranteeing that solely approved entry to the content material is allowed.
- Safe content material supply is important for contemporary internet functions, because it improves person expertise via sooner content material loading instances and provides safety measures to guard static and dynamic content material from unauthorized entry and assaults.
Excessive Availability
- Designing infrastructure with Load Balancers is vital to making sure service continuity and dealing with excessive visitors effectively. Load balancers distribute incoming community visitors throughout a number of servers, stopping any single server from turning into a bottleneck, thus enhancing the supply and reliability of internet companies.
- Excessive availability is essential to backend infrastructure, guaranteeing that internet functions stay accessible even throughout high-traffic durations or when particular person servers fail. This resilience is essential for sustaining person belief and enterprise continuity.
4 API Safety
API safety is a key part of software program safety, guaranteeing that interfaces uncovered for software interactions are safeguarded in opposition to unauthorized entry and assaults. Right here’s a concise overview of securing APIs successfully:
API Authentication and Authorization
- Implement robust authentication mechanisms, comparable to OAuth2, to confirm the identification of API customers, guaranteeing that solely approved customers can acquire entry.
- Implement strict authorization controls to handle what actions authenticated customers can carry out, limiting entry to delicate operations and knowledge throughout the API.
API Fee Limiting
- Implement charge limiting to safeguard in opposition to brute-force assaults and abuse. This includes limiting the variety of requests a person could make to the API inside a particular timeframe, stopping overload, and guaranteeing availability for all customers.
API Monitoring
- Repeatedly monitor API exercise to detect and reply to suspicious conduct. This includes monitoring and analyzing API calls to establish anomalies which will point out potential safety threats or breaches, enabling well timed intervention to mitigate dangers.
5 Safe Deployment Methods
These methods are essential for software program’s dependable and secure supply in at present’s cloud-centric setting. Implementing these methods ensures that functions usually are not solely deployed effectively but additionally maintained in a safe state in opposition to potential vulnerabilities and threats:
Kubernetes and Cloud Deployments
- Adopting GitOps for safe Steady Integration/Steady Deployment (CI/CD) processes represents a paradigm shift in managing deployments and infrastructure as code. GitOps leverages Git as a single supply of fact for declarative infrastructure and functions, enabling automated, predictable, and safer deployments. By integrating safety checks and checks into the CI/CD pipelines, GitOps facilitates a safer and streamlined deployment course of, notably in Kubernetes environments the place configuration and infrastructure administration are essential.
- This method enhances the safety posture by guaranteeing that any adjustments made are auditable, verifiable, and reversible, thereby minimizing the potential for human error and rising the effectivity of deploying and managing cloud-native functions.
Cloud Safety Measures
- Establishing particular safety teams and Id and Entry Administration (IAM) insurance policies is foundational for cloud safety measures. Safety teams act as digital firewalls, for example, controlling inbound and outbound visitors and guaranteeing that solely approved entry is permitted. Equally, IAM insurance policies present granular permissions to customers and companies, guaranteeing that entities have solely the entry wanted to carry out their duties, following the precept of least privilege.
- Utilizing instruments like ClamAV, Rootkit Hunter, and OpenVAS for vulnerability administration performs a pivotal position in figuring out and mitigating threats. These instruments provide completely different capabilities, comparable to malware scanning with ClamAV, detecting rootkits with Rootkit Hunter, and complete vulnerability assessments with OpenVAS, overlaying varied system and community safety points.
- Implementing these cloud safety measures is important for safeguarding infrastructure and knowledge from unauthorized entry, knowledge breaches, and different cyber threats. By proactively managing vulnerabilities and imposing strict entry controls, organizations can considerably scale back their assault floor and improve their total safety posture within the cloud.
6 Complete Monitoring and Logging
Complete monitoring and logging methods are important for sustaining the operational well being and safety posture. These methods allow organizations to detect points, analyze traits, and reply to incidents proactively.
Logging Mechanisms
- Implementing sturdy logging options comparable to Nagios, CloudWatch, Datadog, and the ELK stack (Elasticsearch, Logstash, and Kibana) is essential for detailed monitoring and auditing. These instruments present real-time visibility into system and software efficiency, serving to establish anomalies, efficiency bottlenecks, and potential safety incidents. For instance, Nagios provides intensive monitoring capabilities for community companies, CloudWatch integrates deeply with AWS companies for logs and metrics, Datadog excels in cloud-scale monitoring, and the ELK stack provides highly effective log processing and visualization options.
- Efficient logging mechanisms are foundational for understanding the state of the IT infrastructure, guaranteeing that efficiency points and safety threats could be recognized and addressed promptly, thereby minimizing impression on operations and safety.
Centralized Log Administration
- Aggregating logs from varied sources right into a centralized administration system is vital for enhanced evaluation and gaining deeper safety insights. Centralized log administration simplifies the gathering, storage, and evaluation course of, making it simpler to correlate occasions throughout completely different methods and functions. This complete view aids in detecting complicated safety threats and operational points that may not be obvious when viewing logs in isolation.
- Centralizing logs improves incident response instances and helps compliance with regulatory necessities by guaranteeing that logs are accessible and auditable.
Entry Administration and Log Safety
- Utilizing AWS CloudTrail and configuring strict IAM insurance policies are essential for securing log entry and defending delicate knowledge. CloudTrail offers a historical past of AWS API requires an account, together with actions taken via the AWS Administration Console, AWS SDKs, and command-line instruments, which is significant for safety auditing. By configuring IAM insurance policies, organizations can prohibit log entry to approved personnel, lowering the chance of unauthorized log manipulation or entry.
- Moreover, establishing S3 bucket logging with acceptable retention insurance policies ensures that logs usually are not solely securely saved but additionally retained for a interval that complies with organizational and regulatory requirements. This method to log safety and entry administration is essential for sustaining the integrity and confidentiality of log knowledge, offering a safe framework for logging actions throughout the cloud setting.
7 Information Safety
Information safety is essential to making sure the confidentiality, integrity, and availability of information inside a company.
IAM Insurance policies
- Configure strict IAM (Id and Entry Administration) insurance policies to manage entry to AWS assets. This consists of limiting permissions for server admin accounts to forestall unauthorized entry to delicate knowledge.
Encryption
- Allow encryption for delicate knowledge saved in S3 buckets to guard it from unauthorized entry. This ensures that even when knowledge is compromised, it stays encrypted and unreadable.
AWS CloudTrail
- Monitor all API calls made throughout the AWS setting utilizing AWS CloudTrail. This permits for the monitoring and auditing of person exercise, offering visibility into who accessed what assets and when.
Community Safety Controls
- Implement community safety controls comparable to VPC (Digital Personal Cloud) safety teams and NACLs (Community Entry Management Lists) to limit entry to assets primarily based on IP addresses, subnets, or ports.
Common Safety Audits
- Conduct common safety audits to evaluate the effectiveness of safety measures, establish vulnerabilities, and guarantee compliance with safety finest practices. This consists of reviewing IAM insurance policies, encryption settings, community configurations, and entry controls.
8 Restrict Entry by System
Entry limitation enhances total safety by limiting server entry to trusted units, lowering the chance of unauthorized entry and potential safety breaches.
Community Entry Controls
- Implement strict community entry controls utilizing safety teams or firewall guidelines to limit server entry primarily based on trusted IP addresses or IP ranges. This prevents unauthorized entry from unknown or suspicious units.
Digital Personal Community (VPN)
- Implement a Digital Personal Community (VPN) to determine safe connections between units and servers. Require device-level authentication earlier than granting entry to the server, guaranteeing that solely approved units can set up connections.
Certificates-Based mostly Authentication
- Leverage certificate-based authentication to reinforce safety additional and confirm the identification of units connecting to the server. This includes issuing digital certificates to trusted units, that are then used to authenticate and set up safe connections.
9 Menace Intelligence
Menace intelligence is essential in strengthening a company’s cybersecurity posture, comparable to cybersecurity for internet functions or cell apps. It includes leveraging superior companies and adopting stringent entry management ideas to detect, analyze, and reply to threats extra successfully.
Integrating AWS Safety Companies
- Utilizing a collection of Amazon Internet Companies (AWS) for complete risk detection and response enhances a company’s capability to establish and mitigate safety threats. Amazon GuardDuty provides clever risk detection that screens malicious exercise and unauthorized conduct throughout AWS accounts. AWS Safety Hub aggregates, organizes, and prioritizes safety alerts or findings from a number of AWS companies, offering a consolidated view of safety posture.
- AWS Internet Software Firewall (WAF) protects internet functions from widespread internet exploits that would have an effect on software availability, compromise safety, or devour extreme assets. AWS Defend offers managed Distributed Denial of Service (DDoS) safety, safeguarding functions working on AWS. Collectively, these companies kind a strong protection mechanism in opposition to varied safety threats, from potential knowledge breaches to DDoS assaults, guaranteeing that assets are protected and resilient in opposition to assaults.
IAM for Least Privilege
- Using the precept of least privilege via AWS Id and Entry Administration (IAM) is key to minimizing potential assault vectors. By granting solely the mandatory permissions required to carry out a activity, organizations can considerably scale back the chance of unauthorized entry or escalation of privileges. AWS IAM permits fine-grained entry management to AWS assets, permitting for the precise configuration of who can entry what assets beneath which circumstances.
- Monitoring actions with AWS CloudTrail additional enhances safety by offering a complete log of all person actions and API utilization throughout AWS infrastructure. This permits for detailed auditing, real-time safety evaluation, and the power to reply to suspicious actions shortly. By using least privilege and proactive monitoring, guaranteeing that entry is strictly controbackuplled and that any deviations from anticipated conduct are shortly detected and remediated.
10 Backup
Backup is important in any knowledge administration technique, aiming to guard knowledge from loss or corruption. It ensures knowledge availability, even throughout system failures or cybersecurity breaches. This planning kinds the spine of organizational resilience, safeguarding essential knowledge property.
Database and Server Backups
- Implementing automated backup schedules via companies like AWS Backup is important for guaranteeing that knowledge is recurrently backed up with out counting on guide intervention, thus lowering the chance of information loss. Automated backups could be configured to happen at common intervals, capturing the state of databases and servers and storing this knowledge securely within the cloud. This observe safeguards in opposition to unintentional deletions, {hardware} failures, and knowledge corruption and offers a basis for catastrophe restoration efforts.
- Common testing of backup integrity and restore processes is essential to substantiate that knowledge could be successfully recovered after an incident. This includes periodically restoring knowledge from backups to confirm the information integrity and the effectiveness of the restoration course of. Such checks be sure that backup methods are dependable and that restoration procedures are well-understood and documented, minimizing downtime within the occasion of an precise catastrophe.
11 Information Encryption Methods
Implementing sturdy knowledge encryption measures protects delicate info saved inside databases, safeguarding in opposition to unauthorized entry and guaranteeing compliance with safety requirements.
Choose Encryption Methodology
- Select an acceptable encryption methodology, comparable to Clear Information Encryption (TDE) or encryption-at-rest, primarily based on database sort and necessities.
Allow Encryption
- Use the database administration console or API supplied by the cloud supplier to allow encryption for database cases or storage volumes.
Handle Encryption Keys
- Generate and securely handle encryption keys utilizing a managed service like AWS Key Administration Service (KMS) or by implementing customer-managed keys.
Configure Entry Controls
- Arrange correct entry controls to limit entry to encryption keys, guaranteeing solely approved customers can handle and entry encrypted knowledge.
Monitor Compliance
- Often monitor encryption standing and key administration processes to make sure compliance with safety requirements and mitigate potential safety dangers.
12 Safety Testing
Safety testing is essential to sustaining sturdy software program safety, figuring out vulnerabilities, and guaranteeing that defenses are efficient in opposition to potential assaults. Right here’s a breakdown of important safety testing methodologies:
Penetration Testing
- Penetration testing, or pen testing, simulates cyber assaults in opposition to your software program or community to verify for exploitable vulnerabilities. It includes actively exploiting system weaknesses (e.g., unsanitized inputs and outdated software program parts) to evaluate the effectiveness of current safety measures. This proactive method helps establish the real-world effectiveness of safety controls and may present worthwhile insights into how attackers might breach the system.
Static Evaluation (SAST)
- Static Software Safety Testing (SAST) analyzes supply code or compiled code variations to search out safety flaws with out working this system. SAST instruments scan the code to establish potential safety vulnerabilities comparable to SQL injection, cross-site scripting, and buffer overflows, making it potential to detect points at an early stage within the growth cycle. This methodology is helpful for builders to combine into the CI/CD pipeline for steady safety analysis.
Dynamic Evaluation (DAST)
- Dynamic Software Safety Testing (DAST) assesses functions of their working state. It identifies vulnerabilities that seem in the course of the execution of functions, offering an exterior viewpoint of safety flaws. DAST instruments simulate assaults on internet functions to detect runtime points like authentication and authorization flaws, session administration points, and extra. This method enhances SAST by figuring out solely seen vulnerabilities when the appliance is working.
Safety Scanning
- Safety scanning includes utilizing automated instruments to scan for vulnerabilities inside an software or community. These scans could be a part of static and dynamic analyses, providing common checks for widespread software program safety vulnerabilities, misconfigurations, and safety weaknesses. Safety scanners can be utilized to automate figuring out potential vulnerabilities throughout the software program growth lifecycle (SDLC), guaranteeing steady safety monitoring and enchancment.
Learn Extra: Cybersecurity Finest Practices for Fintech Software program Improvement
Last Ideas
Retaining software program secure is a giant deal in at present’s world of cyber threats. For any software program growth firm, following a safety guidelines is important. By following this complete software program safety guidelines, you’ll be well-equipped to deal with essential safety considerations all through growth. From safe coding practices to sturdy API safety, this information empowers you to develop dependable, scalable, resilient functions in opposition to cyber threats.
However remember that safety is an ongoing course of. Often assessment and replace your safety practices to remain forward of evolving threats. By adopting a tradition of safety consciousness and implementing the methods outlined right here, you’ll be able to scale back the chance of breaches and make sure the long-term success of your software program.

