In in the present day’s digital panorama, internet safety is extra essential than ever. With cyber threats evolving quickly, it’s important for web site homeowners and builders to remain forward of potential vulnerabilities. Whether or not you’re concerned in customized web site improvement or managing an present web site, understanding the newest safety finest practices is essential.
This weblog put up will discover key internet safety finest practices to assist defend your web site from varied assaults, incorporating real-world situations and sensible recommendation.
Understanding the Risk Panorama
Earlier than diving into particular practices, let’s take a look at some sobering statistics that spotlight the significance of internet safety:
- In line with IBM’s Price of a Information Breach Report 2023, the typical price of a knowledge breach reached an all-time excessive of $4.45 million.
- The identical report discovered that 51% of organizations plan to extend safety investments because of a breach.
- Cybersecurity Ventures predicts that cybercrime will price the world $10.5 trillion yearly by 2025, up from $3 trillion in 2015.
These numbers underscore the essential want for sturdy internet safety measures. Let’s discover some finest practices to assist safeguard your web site, with detailed explanations and real-world functions.
1. Hold Software program Up-to-Date
One of many easiest but best safety measures is preserving all software program up-to-date. This consists of:
- Content material Administration Programs (CMS)
- Plugins and themes
- Server software program
- Libraries and frameworks
Common updates usually embrace safety patches for newly found vulnerabilities. Neglecting these updates leaves your web site uncovered to potential assaults.
Actual-world utility:
In 2021, a essential zero-day vulnerability was found in WordPress plugin Fancy Product Designer, put in on over 17,000 websites. Attackers might exploit this to bypass authentication and add malicious information. Websites that promptly up to date the plugin had been protected, whereas people who didn’t had been prone to full web site takeover.
Implementation suggestions:
- Allow computerized updates the place attainable
- Arrange a daily schedule to verify for and apply updates manually
- Use a staging atmosphere to check updates earlier than making use of them to your reside web site
- Hold a list of all software program and their variations to make sure nothing is ignored
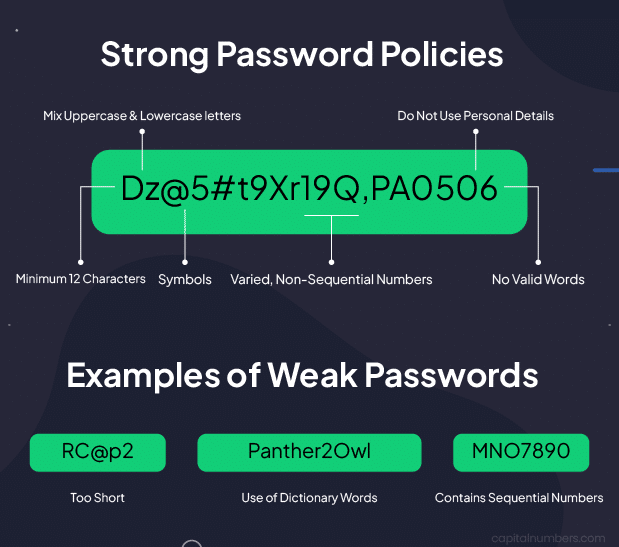
2. Implement Sturdy Password Insurance policies
Weak passwords stay a typical entry level for attackers. Implement robust password insurance policies by:
- Requiring a minimal size (at the very least 12 characters)
- Mandating a mixture of uppercase and lowercase letters, numbers, and particular characters
- Implementing multi-factor authentication (MFA)
- Utilizing a password supervisor to generate and retailer advanced passwords
Actual-world utility:
In 2019, Disney+ accounts had been hacked inside hours of the service’s launch. Many affected customers admitted to reusing passwords from different companies, highlighting the significance of distinctive, robust passwords for every account.
Implementation suggestions:
- Use a good password supervisor like LastPass, 1Password, or Bitwarden
- Implement a password energy meter on registration types
- Require password modifications at common intervals, however not too steadily to keep away from “password fatigue”
- Educate customers on the significance of robust, distinctive passwords
3. Use HTTPS In all places
HTTPS (Hypertext Switch Protocol Safe) encrypts information transmitted between the person’s browser and your web site. This protects delicate info like login credentials and cost particulars from interception.
To implement HTTPS:
- Get hold of an SSL/TLS certificates
- Set up the certificates in your internet server
- Configure your web site to make use of HTTPS by default
- Use HTTP Strict Transport Safety (HSTS) headers
Actual-world utility:
In 2017, Equifax’s information breach, which uncovered delicate info of 147 million individuals, was partly resulting from an expired SSL certificates. This underscores the significance of not simply implementing HTTPS, but additionally sustaining it correctly.
Implementation suggestions:
- Use companies like Let’s Encrypt free of charge SSL certificates
- Implement computerized renewal of SSL certificates to keep away from expiration
- Use instruments like Qualys SSL Labs to check your SSL implementation
- Configure your internet server to redirect all HTTP visitors to HTTPS
4. Implement Internet Utility Firewalls (WAF)
A Internet Utility Firewall acts as a defend between your web site and the web, filtering out malicious visitors. WAFs can defend towards widespread assaults reminiscent of:
- SQL injection
- Cross-site scripting (XSS)
- Cross-site request forgery (CSRF)
- DDoS assaults
Many cloud suppliers and CDNs supply WAF companies that may be simply built-in into your web site’s infrastructure.
Actual-world utility:
Through the 2018 FIFA World Cup, the official web site confronted quite a few cyber assaults. The implementation of a WAF was essential in mitigating these assaults, permitting the location to deal with peak visitors of 4 million requests per second.
Implementation suggestions:
- Contemplate cloud-based WAF options for simpler administration and updates
- Frequently replace WAF guidelines to guard towards new kinds of assaults
- Monitor WAF logs to determine and reply to assault patterns
- Use WAF in studying mode initially to keep away from false positives earlier than switching to blocking mode
5. Observe Safe Coding Strategies
Builders play an important function in web site safety. Some key safe coding practices embrace:
- Enter validation and sanitization
- Parameterized queries to forestall SQL injection
- Correct error dealing with and logging
- Implementing Content material Safety Coverage (CSP) headers
- Utilizing safe session administration strategies
Common code critiques and automatic safety scanning instruments can assist determine potential vulnerabilities in your codebase.
Actual-world utility:
In 2017, Uber disclosed a knowledge breach that uncovered information of 57 million customers. The breach was attainable resulting from hardcoded credentials within the supply code, which allowed attackers to entry Uber’s GitHub repository and subsequently, their AWS servers.
Implementation suggestions:
- Use static code evaluation instruments like SonarQube or Veracode
- Implement peer code critiques with a concentrate on safety
- Comply with the OWASP Safe Coding Practices guidelines
- Frequently practice builders on the newest safe coding strategies
6. Backup Frequently and Securely
Whereas not a direct protection towards assaults, common backups are essential for restoration in case of a profitable breach. Be sure that:
- Backups are carried out steadily (each day for dynamic websites)
- Backup information are encrypted
- Backups are saved in a separate, safe location
- You repeatedly take a look at the restore course of to make sure backups are viable
Actual-world utility:
In 2019, internet hosting supplier A2 Internet hosting suffered a ransomware assault that took down Home windows internet hosting servers. Shoppers with latest, safe backups had been capable of restore their websites shortly, whereas others confronted extended downtime.
Implementation suggestions:
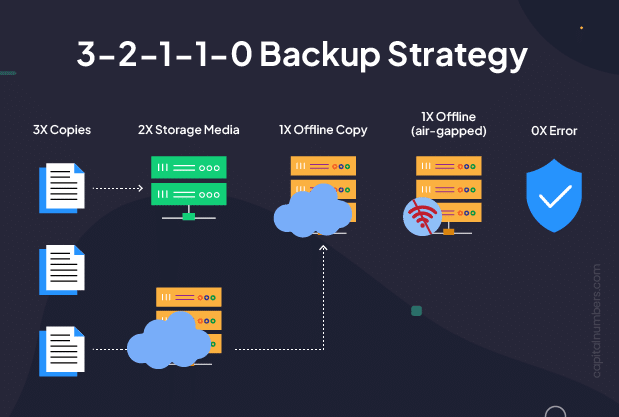
- Implement the 3-2-1 backup technique: 3 copies of information, on 2 totally different media, with 1 copy offsite
- Use automated backup options to make sure consistency
- Encrypt backups each in transit and at relaxation
- Frequently carry out restore drills to make sure backup integrity
7. Monitor and Log Exercise
Implementing sturdy logging and monitoring methods can assist you detect and reply to safety incidents shortly. Key areas to watch embrace:
- Failed login makes an attempt
- File system modifications
- Database queries
- Community visitors patterns
Use instruments like intrusion detection methods (IDS) and safety info and occasion administration (SIEM) options to combination and analyze logs successfully.
Actual-world utility:
The 2013 Goal information breach, which uncovered 40 million bank card numbers, might have been mitigated if the corporate had correctly monitored and responded to safety alerts. Their methods detected the malicious exercise, however the alerts weren’t acted upon.
Implementation suggestions:
- Centralize logs utilizing instruments like ELK stack (Elasticsearch, Logstash, Kibana) or Splunk
- Arrange alerts for suspicious actions
- Frequently overview and analyze logs for patterns or anomalies
- Guarantee logs are saved securely and can’t be tampered with
8. Educate Your Staff
Human error stays one of many largest safety dangers. Common coaching classes on your workforce can assist mitigate this danger. Cowl subjects reminiscent of:
- Recognizing phishing makes an attempt
- Secure shopping practices
- The significance of updating software program
- How you can deal with delicate information
Actual-world utility:
In 2020, Twitter suffered a serious breach the place high-profile accounts had been compromised. The assault was profitable resulting from a social engineering assault on Twitter workers, highlighting the significance of workers schooling in cybersecurity.
Implementation suggestions:
- Conduct common safety consciousness coaching classes
- Use simulated phishing campaigns to check and educate workers
- Create and implement clear safety insurance policies and procedures
- Foster a tradition of safety consciousness throughout the group
You Might Additionally Learn: WordPress Safety: Superior Strategies and Greatest Practices
A Private Expertise: Studying the Exhausting Method
Whereas I don’t have private experiences, let me share a hypothetical situation that illustrates the significance of those safety practices:
- As a junior developer at a small e-commerce startup, I used to be tasked with constructing our firm’s first web site. Excited in regards to the options and design, I rushed via the event, neglecting most of the safety practices talked about above.
- Two months after launch, catastrophe struck. We awoke one morning to search out our web site defaced, buyer information stolen, and our fame in tatters. The assault exploited a number of vulnerabilities:
- We had used an outdated model of our CMS, which had a identified vulnerability.
- Our admin password was weak and simply guessed.
- We hadn’t carried out HTTPS, permitting attackers to intercept login credentials.
- Our backups had been irregular and never correctly secured.
- The aftermath was devastating. We spent weeks rebuilding the location, coping with offended clients, and making an attempt to salvage our fame. The monetary price was important, however the lack of belief was much more damaging.
- This expertise taught me the onerous method that safety isn’t an afterthought—it’s a basic side of internet improvement. Since then, I’ve made it my mission to prioritize safety in each mission, following the perfect practices outlined on this put up.
You Might Additionally Learn: Don’t Get Hacked: Important Software program Safety Guidelines for Builders
Conclusion
Internet safety is an ongoing course of, not a one-time process. By implementing these finest practices and staying knowledgeable about rising threats, you possibly can considerably scale back the chance of your web site falling sufferer to cyber assaults.
Bear in mind, the price of prevention is at all times decrease than the price of restoration from a profitable assault. Spend money on your web site’s safety in the present day to guard your corporation and your customers’ belief tomorrow.
Because the menace panorama continues to evolve, so too should our safety practices. Keep vigilant, continue learning, and by no means assume your web site is “safe sufficient.” On the earth of internet safety, complacency is the enemy of security.
Don’t watch for a breach to occur – take motion now to fortify your web site’s safety. Contact us in the present day to find out how we can assist you safeguard your on-line presence.

